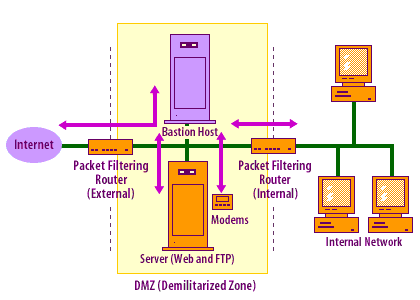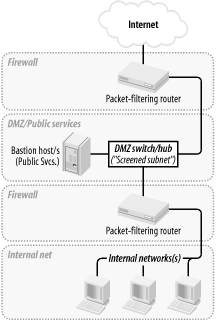
Section 2.2. Types of Firewall and DMZ Architectures :: Chapter 2. Designing Perimeter Networks :: Secure Linux-based Servers :: Linux systems :: eTutorials.org

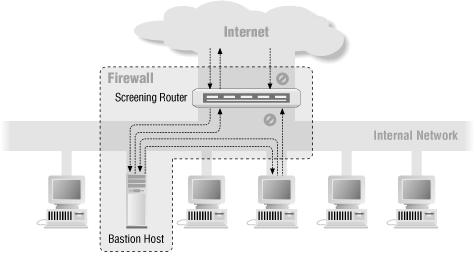
GSNA Exam Dumps | HOTSPOT In the image of the Screened Host Firewall Architecture given below, select the element that

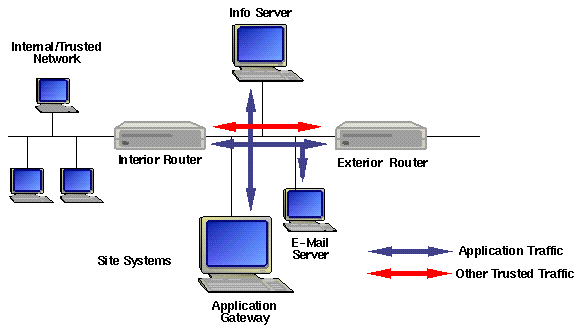
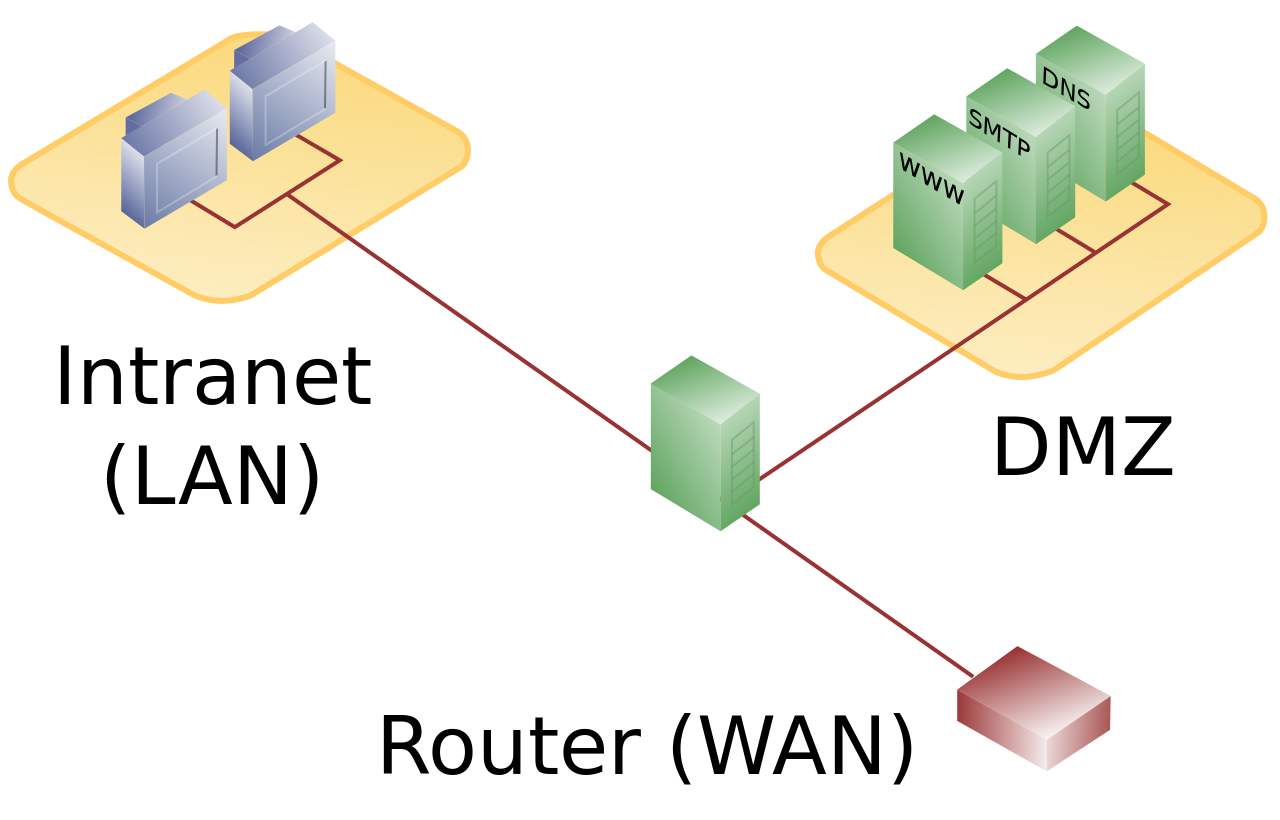
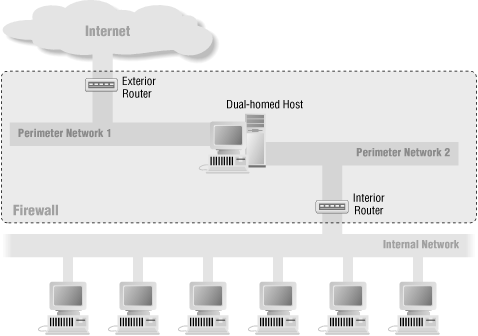
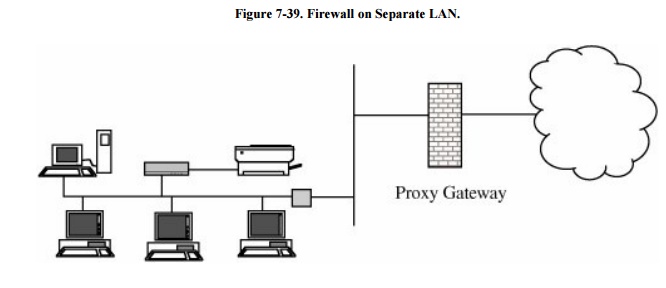
![Chapter 4] 4.2 Firewall Architectures Chapter 4] 4.2 Firewall Architectures](https://docstore.mik.ua/orelly/networking/firewall/figs/fire0404.gif)


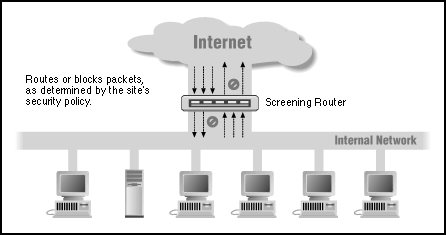
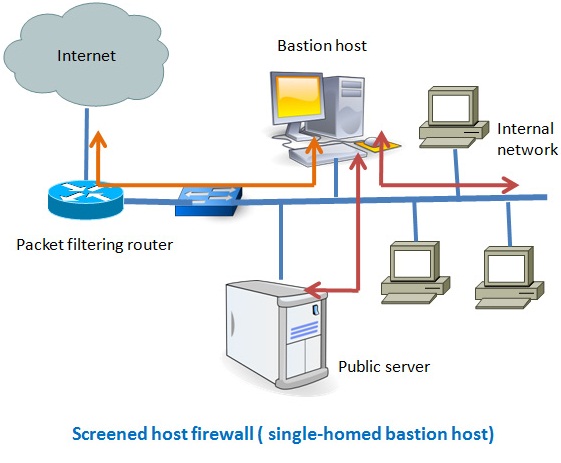



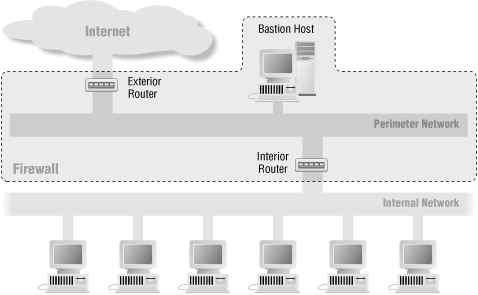
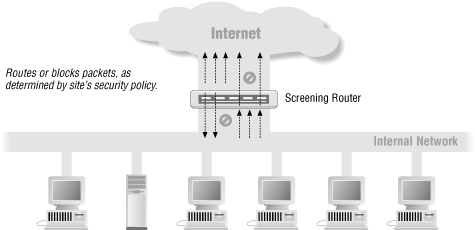
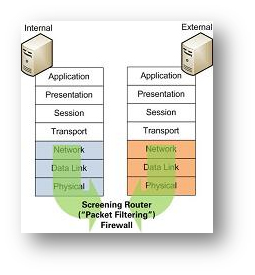
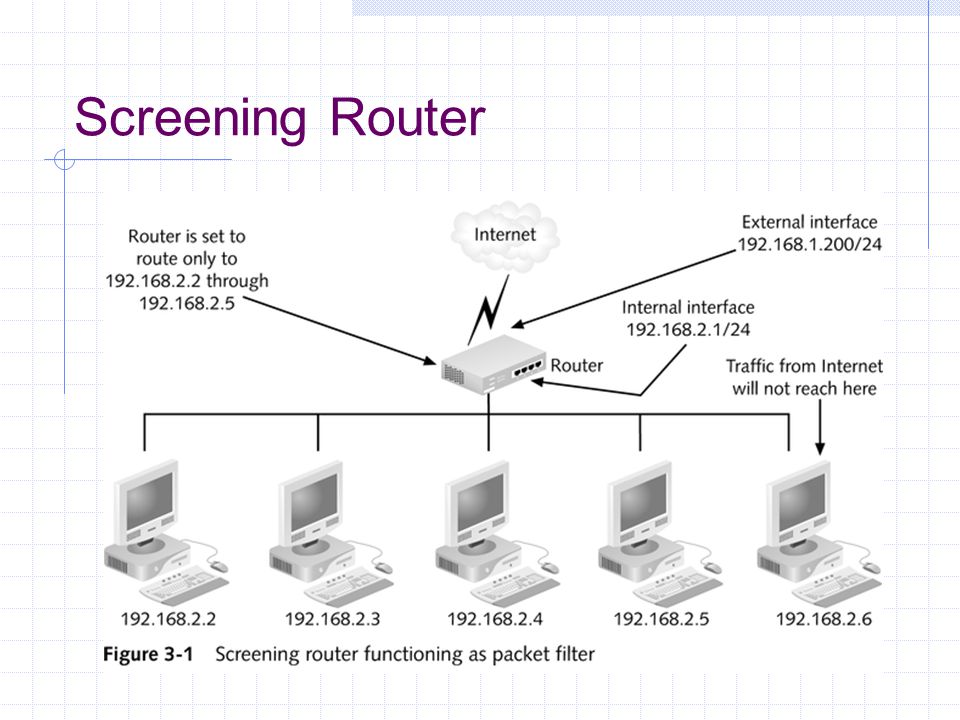


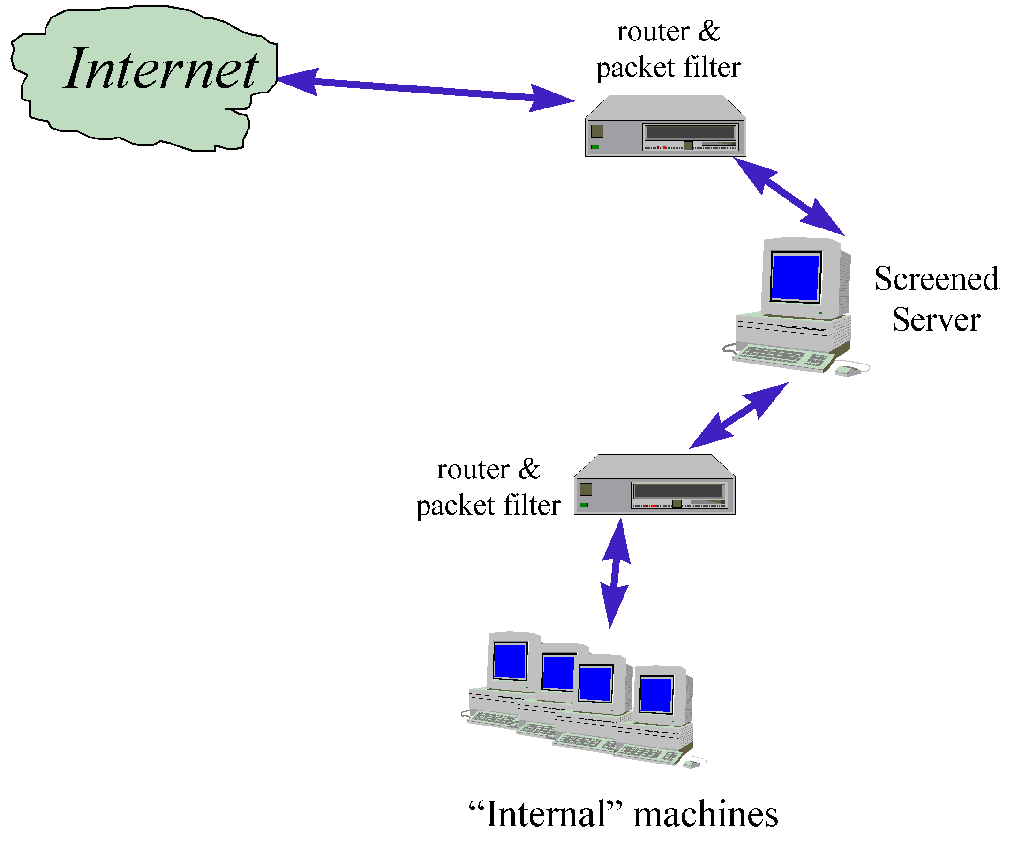
![Chapter 6] Packet Filtering Chapter 6] Packet Filtering](http://web.deu.edu.tr/doc/oreily/networking/firewall/figs/fire0601.gif)